satya - 3/25/2019, 1:38:13 PM
Example of signing

By FlippyFlink - Changed the image https://en.wikipedia.org/wiki/File:Public_key_encryption.svg from encryption to signing., CC BY-SA 4.0, Link
It is often, occasionally followed by a wave of hand, that one advises or talks of "jar" (packaged java files that makes up an application or module) files as being signed.
Few times we ask back: "What do you mean by signed"?
What does it mean for a jar file to be signed?
Does this signing has parallels to how we sign physical documents? Do they differ? How do they differ if they do?
How do you establish a "pattern? of understanding for digital signatures so that you treat the subject abstractly just like when someone says they signed a physical document?
Imagine you are a wine collector located in a very un-wine-like place such as Sahara desert. And farmers around the world are sending you wine caskets either to archive sell etc. For a moment think that they are not doing it for money. So they will not expecting anything in return.
What the wine collector notices is that each casket he receives and the wine inside it has a specific hue and color that is distinct from another. On further investigation she finds out that if two caskets or wine inside them has the same hue then it ALWAYS comes from the same farmer. On digging further the collector finds out that each farmer has a "SECRET HUE RECIPE? that she locks up in a cellar and never reveals. This explained why each wine is different and that if two wines have same hue they MUST COME from the same farmer.
So the hue becomes a signature of the farmer. And that the farmer hides the signature from everyone else. Like a family stamp.
An important distinction in this example is there is no way for the collector to know "WHICH? farmer sent the wine. For example there is no name, or address associated with that signature. Even if there were it is quite possible that another wine farmer could send by copying that address. The collector will then assume that these two wine caskets that came to her with the same address but clearly has two different hues, that there are two farmers at the same address with the same name but never the same wine.
When I or you sign a document and send it to say to IRS, IRS assumes that you are sending the right information such as phone and address and Social. If two applications are received with the social but signatures are distinct IRS will have to verify your signature with the card that THEY issued.
Same thing with banks. The banks have your signature to verify.
In cases where they don?t preregister your signature they will have to come to you as after the fact and verify the signature later.
It is also reasonable to assume that occasionally physical signatures can be forged. It is far far far harder to crack the digital encryption.
So when someone says that they signed a jar file, it means that this jar file is uniquely colored and can be distinguished from other set of jar files UNIQUELY. However there is no way to identify the source developer or company with authenticity.
Such jar files are called self signed jar files.
To know the "SOURCE?, what you have to do is, have a third party company that the wine collector trusts tell us that the "color-red? comes from "Company1?. Now every time we see "color-red? then we know that it is from "Company1?. These are called third party signed jar files. These are useful in your browsers to tell you that you are downloading a file from company 1.
The above semantics or understanding is technically implemented through what is called a Public/Private Key encryption. Mathematics has the ability (with great probability) to generate two numbers where by if you encode with the first number (private) then only the second number (public) can decrypt it. These keys are asymmetric. Even if everyone knows the public key there is NO way they can encrypt a message that the Public key can decrypt. Only its matching private key can do that.
So in essence when the wine farmer creates a code for his casket using the private key, she writes down the public key name on top of the casket and also the secret code on the casket. When the wine collector takes that public key and unravels the secret code, if she is successful then she knows that the "public? key is correct and the message is only encrypted by the farmer who wrote the public key.
The first one "keytool? generates the public/private keys given a password.
The second tool called "jarsigner? creates the secret code using the private key and the jar file data itself. This additional step of including the jar file contents enables the jar file being untampered.
When you visit a foreign land, you turn on the radio, and you hear many different songs. You can tell there are different singers and you can identify each separately but not know who they are or know their names. This is also self signing. When a friend of yours tells you a singer and associates to a voice you have heard that is third party signing.
Again one can imitate another singers voice to confuse or lull the listener to incompetence where as it is far far far harder to emulate a digital signature.
1. Signing android applications
2. My notes on understanding android apk files
3. A greate read from Sun/Oracle on keytool and signing
satya - Wednesday, April 13, 2011 11:06:28 AM
Why self-signed digital signatures?
A discussion on Android Developers group
Why self-signed digital signatures?: A discussion on Android Developers group
satya - 1/17/2014 10:11:28 AM
Read about PKI (Public Key Infrastructure) here
satya - 3/25/2019, 1:38:13 PM
Example of signing

By FlippyFlink - Changed the image https://en.wikipedia.org/wiki/File:Public_key_encryption.svg from encryption to signing., CC BY-SA 4.0, Link
satya - 3/25/2019, 1:39:26 PM
A definition of a certificate
A certificate is a digitally signed statement from one entity (person, company, etc.), saying that the public key (and some other information) of some other entity has a particular value. (See Certificates.) When data is digitally signed, the signature can be verified to check the data integrity and authenticity. Integrity means that the data has not been modified or tampered with, and authenticity means the data indeed comes from whoever claims to have created and signed it.
satya - 3/25/2019, 1:51:46 PM
X.509 certificate has the followingg
version
Serial number
algorithm used
Who issued it: CA
Valid till:
Subject Name: Whose signature is this
Ex: Oracle
Public Key
satya - 3/25/2019, 1:52:39 PM
How do you verify a digital signature?
How do you verify a digital signature?
satya - 3/25/2019, 2:05:34 PM
What is a digital signature
A digital signature in its simplest description is a hash (SHA1, MD5, etc.) of the data (file, message, etc.)
that is subsequently encrypted with the signer's private key.
Since that is something only the signer has (or should have) that is where the trust comes from
EVERYONE has (or should have) access to the signer's public key.
satya - 3/25/2019, 2:26:39 PM
how do you verify a self signed jar file signature
how do you verify a self signed jar file signature
Search for: how do you verify a self signed jar file signature
satya - 3/25/2019, 2:27:07 PM
Here is how to use jarsigner: a doc
satya - 3/25/2019, 2:28:30 PM
why this search?
I am missing the details.
I know that a jar is signed with a private key.
how could one verify without mentioning what the public key is? where is the public key mentioned in the verification process? is there a difference if it is signed by a trusted third party?
satya - 3/25/2019, 2:30:10 PM
Here is much more detailed explanation
satya - 3/25/2019, 2:30:38 PM
As expected
Before you can use the jarsigner tool to check the authenticity of the JAR file's signature, you need to import Stan's certificate into your keystore
satya - 3/25/2019, 2:37:34 PM
Here is how this works using a certificate authority
satya - 3/25/2019, 2:38:55 PM
Difference between self signed jar files and CA signed jar files
Difference between self signed jar files and CA signed jar files
Search for: Difference between self signed jar files and CA signed jar files
satya - 3/25/2019, 2:53:03 PM
Here is the selfsigning process
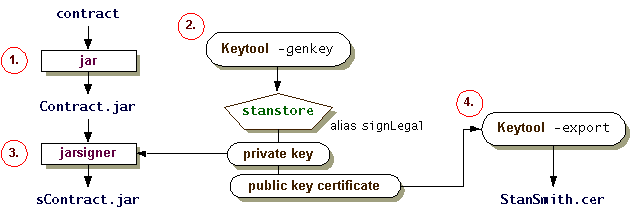
satya - 3/25/2019, 2:53:15 PM
Notice the two files
Notice the two files
satya - 3/26/2019, 9:39:02 AM
where is the public cert kept in a signed executable or jar file?
where is the public cert kept in a signed executable or jar file?
Search for: where is the public cert kept in a signed executable or jar file?
satya - 3/26/2019, 9:41:02 AM
where is the public cert kept in a signed executable file?
where is the public cert kept in a signed executable file?
Search for: where is the public cert kept in a signed executable file?
satya - 3/26/2019, 9:42:56 AM
Introduction to code signing from Microsoft
satya - 3/26/2019, 9:53:52 AM
Signing
Signing data does not alter it; it simply generates a digital signature string you can bundle with the data.
satya - 3/26/2019, 9:54:26 AM
Summary of signing
A one-way hash of the document is produced.
The hash is encrypted with the private key, thereby signing the document.
The document and the signed hash are transmitted.
The recipient produces a one-way hash of the document.
Using the digital signature algorithm, the recipient decrypts the signed hash with the sender's public key.
satya - 3/26/2019, 9:56:02 AM
Where is the public key?
A certificate is a set of data that completely identifies an entity, and is issued by a certification authority only after that authority has verified the entity's identity. The data set includes the entity's public cryptographic key. When the sender of a message signs the message with its private key, the recipient of the message can use the sender's public key (retrieved from the certificate either sent with the message or possibly available elsewhere in the directory service) to verify the sender's identity.
satya - 3/26/2019, 9:59:38 AM
How is a cert obtained
satya - 3/26/2019, 10:00:59 AM
CRL: Revoked certification list
A certificate is valid only for the period of time specified by the certification authority that issued it. The certificate contains information about its beginning and expiration dates. The certification authority can also revoke any certificate it has issued and maintains a list of revoked certificates. This list is called a certificate revocation list (CRL), and is published by the certification authority so that anyone can determine the validity of any given certificate.
satya - 3/26/2019, 10:02:51 AM
How is the public cert chain maintained?
How is the public cert chain maintained?
satya - 3/26/2019, 10:05:27 AM
What is the digital signature format?
What is the digital signature format?
satya - 3/26/2019, 10:11:32 AM
Example of a x.509 cert
Example of a x.509 cert
satya - 3/26/2019, 10:18:06 AM
Does a digital signature include the public cert of the signer?
Does a digital signature include the public cert of the signer?
Search for: Does a digital signature include the public cert of the signer?
satya - 3/26/2019, 10:18:31 AM
file structure of a digital signature?
file structure of a digital signature?
satya - 3/26/2019, 10:20:39 AM
Issuer name of a x.509 certificate
Issuer name of a x.509 certificate
satya - 3/28/2019, 11:25:46 AM
The above link has a printout of the x.509 certificate
The above link has a printout of the x.509 certificate
Link repeated.
satya - 3/28/2019, 11:29:44 AM
Few take aways
x.509 is plain text
Follows ASN.1 specification both in terms of structure and language (like say XML)
If Issuer is the same as subject it is likely self signed
Public key is in plain text
There is signature in it. This got to be the rest of the data, hashed first, and encrypted with the private key of the self signer. So if we take the public key and decrypt it and match it to the hash they should match.
satya - 3/28/2019, 11:36:39 AM
thumbprint
It is a computed field of the hash value of the data in x.509
it is called cert hash sometimes
it is a hash of the whole cert that contains all the parts(Cert, Signature Algorithm, Signature)
satya - 3/28/2019, 11:38:19 AM
That answers one question, what is signature of a cert and where is it kept?
So it is the encrypted hash of the other cert data
It is stored in the cert itself
this signature is the signature of the "Cert", and NOT the signature of any file the owner of this public key has encrypted with the private key.
satya - 3/28/2019, 11:41:28 AM
Ref link: technet library, how certs work
satya - 3/28/2019, 11:46:21 AM
how signature works (data not modified)
.gif)
satya - 3/28/2019, 11:48:36 AM
digital signature ASN
digital signature ASN
satya - 3/28/2019, 11:54:18 AM
A digital signature appears to be just a series of bytes
A digital signature appears to be just a series of bytes
satya - 3/28/2019, 11:55:07 AM
does a digitally signed jar file contain the digital certificate as well?
does a digitally signed jar file contain the digital certificate as well?
Search for: does a digitally signed jar file contain the digital certificate as well?
satya - 3/28/2019, 11:59:09 AM
understanding signing of jar files
understanding signing of jar files
This has the following statement: When you sign a JAR file your public key is placed inside the archive along with an associated certificate so that it's easily available for use by anyone wanting to verify your signature.
satya - 3/28/2019, 11:59:29 AM
The above document further states
satya - 3/28/2019, 12:03:11 PM
The signature block file contains two elements essential for verification:
satya - 4/3/2019, 12:04:40 PM
Here is diagram of how to know if an installation file is good